I was told earlier there wasn’t much on the internet detailing this configuration so decided to throw a quick post together. I may expand on it later to add detail as to how this works and why you would choose OAuth instead of the more common SAML configuration if anyone is interested (Drop me a tweet if you are – @stuart_carroll.
This post will detail how to configure an existing Citrix ADC Gateway or AAA vserver to authenticate using Azure AD OAuth.
First we need to create an App Registration in Azure AD for our Citrix ADC service
- Log in to Azure Portal and select Azure Active Directory
- Select ‘App Registrations’ from the menu
- Select ‘New Registration’
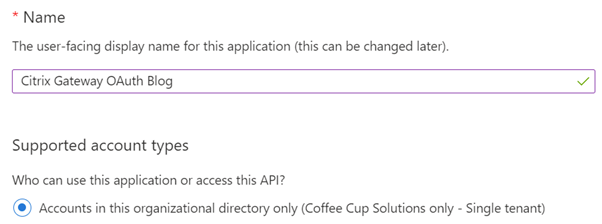
- Enter a name for you app registration and select the relevant ‘Supported account type’ – In this example we only want users from this a single Azure AD Tennent.
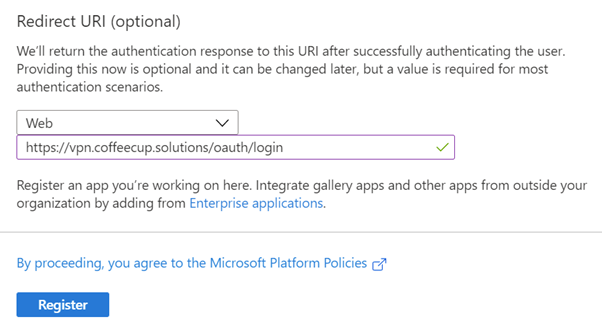
- Select ‘Web’ from the Redirect URI drop down menu and enter your redirect URI, This will be you’re the FQDN of your Citrix Gateway virtual server with ‘/oauth/login’ as the URL – example: https://FQDN/oauth/login https://vpn.coffeecup.solutions/oauth/login
- Select Register
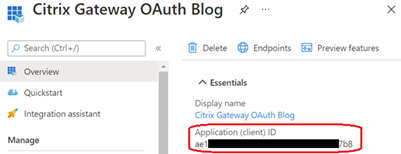
- From the ‘Overview’ page for the app registration there will be an Application ID. Take a note of this, it will be your OAuth Client ID when you configure your OAuth Profile on the Citrix Gateway
- Select ‘Endpoints’ and copy the following values, when you configure your OAuth Profile on the Citrix Gateway
- OAuth 2.0 authorization endpoint (v2), this is the auth URL.
- OAuth 2.0 token endpoint (v2), this is the token URL.
- Select ‘Certificates & Secrets’ and selecting ‘New client secret’
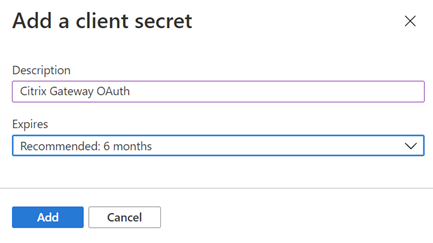
- Enter a name for your client secret, select an expiry period from the ‘Expires’ drop down menu and select ‘Add’.
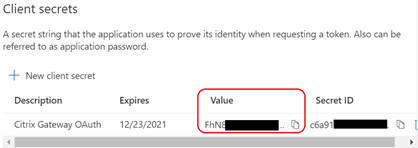
- Take a note of the Secret Value, it will be your client secret when you configure your OAuth Profile on the Citrix Gateway
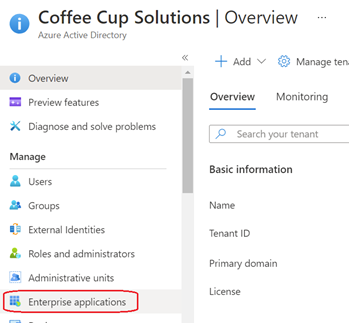
- Return to the Azure Active Directory management page and select ‘Enterprise applications’
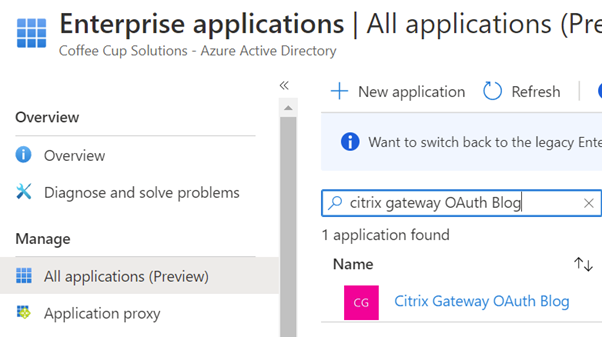
- Find and select the enterprise app you have just created
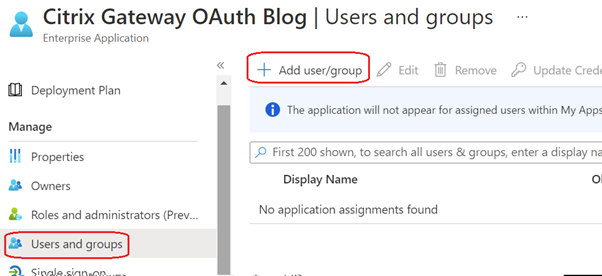
- Select ‘Users and groups’ and add users or groups you wish to authenticate to your Citrix Gateway
That’s is for Azure Active Directory – Now onto the Citrix ADC. This blog assumes you have a working Citrix Gateway configured with no authentication currently configured and an existing AAA virtual server.
You cannot bind an OAuth authentication policy directly to a Citrix Gateway virtual server so you will need to configure and bind the OAuth authentication policy to a AAA virtual server and use an Authentication Profile to link the Gateway vserver with the AAA vserver.
- Log onto your Citrix ADC
- Browse to the ‘Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy’ and Select ‘Add’
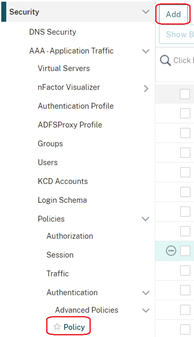
- Enter the following details in your Authentication Policy:
- Enter a name for your authentication policy
- Select ‘OAUTH’ from the ‘Action Type’ drop down menu,
- Enter ‘true’ in the expression test box
- Select ‘Add’ next to the ‘Action’ drop down menu to create you Authentication Action
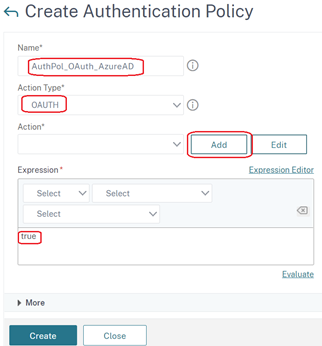
- Enter the following details in your Authentication Action:
- Name
- Select ‘GENERIC’ from the ‘OAuth Implementation Type’ drop down menu
- Enter the ‘Application (Client) ID’ taken from your Azure AD App Registration in the ‘Client ID’ field
- Enter your App Registration Secret value in the ‘Client Secret’ field
- Leave the ‘Authentication’ drop down menu set to ‘ENABLED’
- Enter your App Registration ‘OAuth 2.0 authorization endpoint (v2)’ Endpoint URI in the ‘Authorization Endpoint’ field
- Enter your App Registration ‘OAuth 2.0 token endpoint (v2)’ Endpoint URI in the ‘Token Endpoint’ field
- Select ‘Create’ to create the action
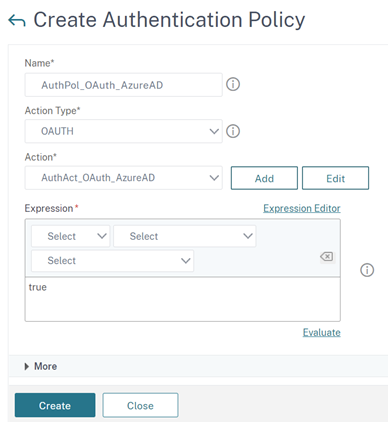
- Select ‘Create’ to create the Authentication policy
- Browse to the ‘Security > AAA – Application Traffic > Virtual Servers’ node in the Citrix ADC UI
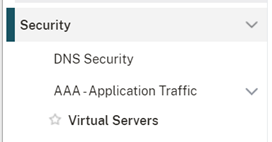
- Select your AAA virtual server and select ‘Edit’
- Select ‘No Authentication Policy’ to bind your new OAuth authentication policy
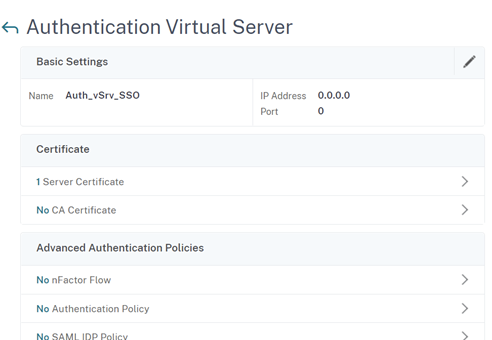
- Select the new OAuth Policy from the ‘Select Policy’ menu, Select ‘Bind’ and select done.
If you are configuring for just AAA then congratulations, you’re done!
If you are configuring OAuth authentication for Citrix Gateway we need to create an Authentication Profile to get the Citrix Gateway vserver to authenticate using the AAA virtual server.
- Browse to the ‘Citrix Gateway > Virtual Servers’ node in the Citrix ADC UI
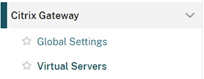
- Select your Citrix Gateway virtual server and select ‘Edit’
- Select ‘Authentication Profile’ and Select ‘Add’
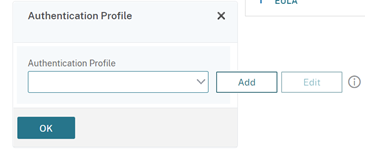
- Enter a name for you Authentication Profile and select your AAA virtual server from the ‘Authentication Virtual Server’ menu and select ‘Create’
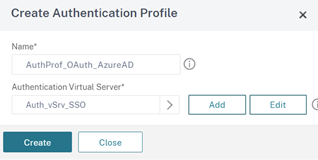
- Select the Done on the Gateway virtual server.
- Browse to your Citrix Gateway virtual server FQDN. You will be redirected to an Azure AD page and the first time to consent to the user of this App Registration on behalf of your organization. Select ‘Accept’
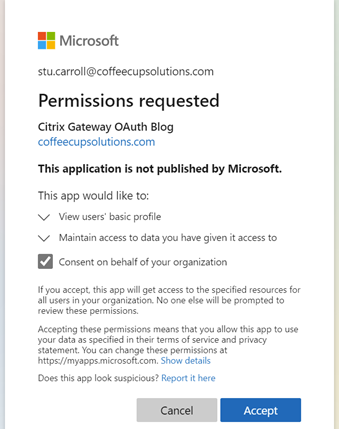
Now you’re done!
Hopefully this has been helpful.
